Firewall Configuration and Attack
- Lab Overview
- Attacking the Server
- Filtering an IP Address
- Filtering TCP Traffic
- Firewall Misconfiguration
- Another Firewall Misconfiguration
- Exercises
Lab Overview
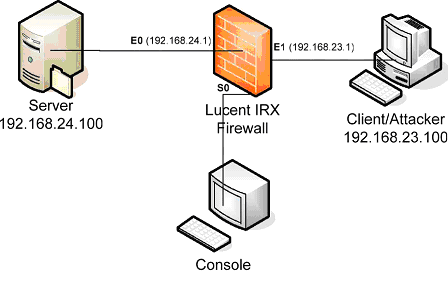
The goal of this tutorial is to allow you to exploit an active attack on the network and implement a simple firewall rule set that will prevent this kind of attack. You will also perform the basic firewall functions. This tutorial is used in Network Security TELECOM 2821.
Required Equipment
To complete this tutorial you will need one PC running Linux OS with a server function (Yucca), one PC running Linux OS with a client and an attacker functions (Periwinkle), one PC running Windows with a console function, and one Lucent Firewall IRX Router. This can all be found in the lab.
Introduction
How do you secure the valuable information within your company’s Intranet while allowing your employees to have access to the outside information they need? How can you reduce your vulnerability to attacks when you have a DSL connection that brings more bandwidth to your house 24 x 7? The solution to both of these problems is found in a firewall by protecting a computer or entire network by limiting what information can get into or leave the network. The role of the firewall in a network is becoming greater as malicious hackers find new exploits for systems.
Firewalls are becoming greater as malicious hackers find new exploits that allow them to compromise a system. Firewalls are either hardware or software. In this tutorial you will be dealing with a hardware firewall from Lucent Technologies. A hardware firewall is a standalone system that is placed between the internal network and the Internet. The network administrator sets the firewall’s attributes to correspond with the desired security policies, which can allow almost all traffic into and out of the network, or deny all incoming and most outgoing traffic. The job of the network administrator is to find the correct balance.
In this tutorial, you will learn how to set-up the firewall for different purposes, perform one type of DOS attacks one a server, and measure the performance of the system. You will also see the effect of a misconfigured firewall rule set. At the end of this tutorial you will design a rule set with a specified, simple network configuration.
Configuring the Console Computer:


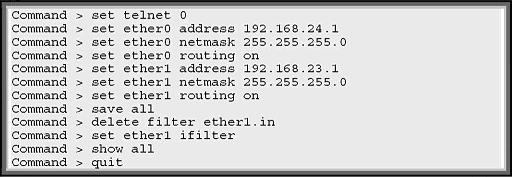
Configuring the Client Computer
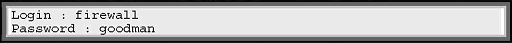
Open the client computer and log-in using:
Attacking the Server
Attacking the Server Without a Firewall
Open 6 terminals on the client and resize them within one window so that you can see all the terminals. In five terminals, type the following command:

Check to see if any of the ping packets got through the firewall. In the 6th terminal, open an FTP connection to the server using the following command and log-in information.
$ ftp 192.168.24.100
Username : firewall
Password : goodguy
After you have logged-in to the FTP server, use command as follow to retrieve a file.
ftp> binary
ftp> get firewall.doc
Record the total time of the transmission. Repeat this process three times.
Repetition Time (sec.)
1 __________________
2 __________________
3 __________________
AVERAGE TIME : __________________________ FILE SIZE : __________________ Bytes
Using the following command to quit the FTP connection.
ftp> bye
Use Ctrl-C to quit the PING process in the other five terminals.
Attacking the Server With a Firewall
Configure the console computer.
- Log-in or continue the session
- Type in the following configuration settings:
> add filter ether1.inTo show the rules, which were entered to the firewall use Command > show filter ether1.in
> set filter ether1.in 1 permit tcp 192.168.23.0/24
> set ether1 ifilter ether1.in
> save filter
Configuring the client computer
- Follow the previous steps to attack the server with a firewall that you used to Attack the Server Without a Firewall.
- Record the total time of the transmission. Repeat this process three times.
Repetition Time (sec.)
1 __________________
2 __________________
3 __________________
AVERAGE TIME : __________________________
Questions
- Explain the attack and discuss the results when compared with those of the section above, Attack the Server Without a Firewall.
- What is the message returned by the PING command and why was this the message returned? You answer should be based on the configuration above.
- Assume that there are two subnets, i.e., 192.168.22.0 and 192.168.23.0. Is it possible for a subnet 192.168.22.0 to ftp this server? Why?
An Alternative Rule Set
- At the console computer, type in the commands as follows:
> delete filter ether1.in
> add filter ether1.in
> set filter ether1.in 1 deny icmp
> set filter ether1.in 2 permit tcp
> set ether1 ifilter ether1.in
> save filter - Repeat the steps found in Attack the Server Without a Firewall section.
- Record the total time of the transmission. Repeat this process three times.
Repetition Time (sec.)
1 __________________
2 __________________
3 __________________
AVERAGE TIME : __________________________
Questions
- Do you see any different in the results between this step and the previous step in the section Attack the Server With a Firewall? Why?
- Assume that there are two subnets, i.e., 192.168.22.0 and 192.168.23.0. Is it possible for a subnet 192.168.22.0 to ftp to this server? Why?
Filtering an IP Address
Configuration
Configuring the console computer.
- Log-in or continue the session
- Type in the commands as follows:
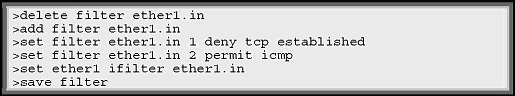
Questions
On the client computer can you
- Open the FTP connection __________
- Open the telnet connection __________
- PING to the server __________
To open a telnet connection use : $ telnet 192.168.24.100
Filtering TCP Traffic
Configuration
Configuring the console computer:
- Log-in or continue the session
- Type in the following commands:
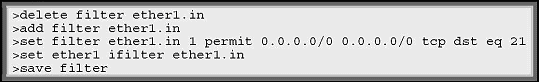
This filter will allow TCP traffic from any host to any destination to connect to a destination port number 21, which is an FTP port number. The syntax for this rule is:
>set filter [filter name] [rule number] [permit/deny] [source address]
[destination address] [tcp/udp/icmp] [src/dst] eq [port number]
Use 0.0.0.0/0 as all network addresses
Questions
On the client computer can you
- Open the FTP connection __________
- Open the telnet connection __________
- PING to the server __________
Firewall Misconfiguration
Configuration
Configuring the console computer:
- Log-in or continue the session.
- Type in the following commands.
>delete filter ether1.in
>add filter ether1.in
>set filter ether1.in 1 permit icmp
>set filter ether1.in 2 deny icmp
>set ether1 ifilter ether1.in
>save filter
Questions
On the client computer can you
- Open the FTP connection __________
- Open the telnet connection __________
- PING to the server __________
A Different Configuration
Configuring the console computer.
- Log-in or continue the session.
- Type in the following commands.
>delete filter ether1.in
>add filter ether1.in
>set filter ether1.in 1 deny icmp
>set filter ether1.in 2 permit icmp
>set ether1 ifilter ether1.in
>save filter
Questions
On the client computer can you
- Open the FTP connection __________
- Open the telnet connection __________
- PING to the server __________
- Discuss the results from the two different configurations.
Another Firewall Misconfiguration
Configuration
Configuring the console computer:
- Log-in or continue the session.
- Type in the following commands:
>delete filter ether1.in
>add filter ether1.in
>set filter ether1.in 1 permit icmp
>set filter ether1.in 2 deny 192.168.23.100/32
>set ether1 ifilter ether1.in
>save filter
Questions
On the client computer can you
- Open the FTP connection __________
- Open the telnet connection __________
- PING to the server __________
Second Configuration
Configuring the console computer:
- Log-in or continue the session.
- Type in the following commands:
>delete filter ether1.in
>add filter ether1.in
>set filter ether1.in 1 deny 192.168.23.100/32
>set filter ether1.in 2 permit icmp
>set ether1 ifilter ether1.in
>save filter
Questions
On the client computer can you
- Open the FTP connection __________
- Open the telnet connection __________
- PING to the server __________
- Discuss the results from the two different configurations.
Exercises
Problem 1
Based on the results in this lab, what is the default rule set for this firewall? (Hint: If an incoming packet is not specified in a rule set, what will the firewall do?
Problem 2
What is the type of this Lucent Firewall IRX router?
Problem 3
Assume that we have a cooperate network as shown in the figure below.
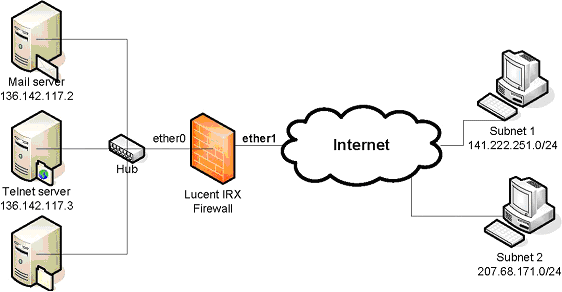
A specific rule set at the incoming connection from the Internet (ether 1) is required to protect the main office network. Design a rule set for all of the requirements below with the Lucent IRX Firewall using example syntax from this tutorial. (Hint: Ordering is important, you may have more or less than 10 rules.)
You need to have rules as follow:
- Only allow 2 subnets are allowed to connect to all servers
- Only a specific port is opened at each type of server
- No ping traffic is allowed to all servers
- 141.222.251.83 and 207.68.171.245 are attacker’s addresses. Block them.
- Deny all inside IP addresses to come in from an outside network
- Port Numbers are: FTP port = 21, Telnet port = 23, and Simple Mail Transfer port = 25
The FTP server is 136.142.117.4







