DATA PRIVACY AND DATA ANALYTICS:
As many analytics in the
Cloud operate on datasets that can be potentially sensitive and private,
allowing human data analysts to perform business analytics on raw data in the Cloud
may lead to privacy breaches even if the datasets are anonymized through
well-known anonymization techniques such as k-anonymization
and differential privacy. In a cloud
both data access needs to be private as well as data processing needs to be
private no matter if the access is from an application running in the same
Cloud or from a remote client device such as a mobile phone.
MobiMix: Protecting Location privacy with Road Network Mix-zones:
When it
comes to Mobile Cloud computing, one family of applications specifically raises
concern. When mobile users in a Cloud request location dependent data services
that require the locations of the clients for processing, a malicious adversary
can utilize the location trace to invade the privacy of the user. MobiMix is a
novel road-network mix-zone based framework for anonymizing location data and
serving location based service requests without disclosing privacy in
real-time. In contrast to spatial cloaking based location privacy protection,
the MobiMix approach aims at breaking the continuity of location exposure
through the development of attack resilient road network mix-zones. However
unlike the theoretical mix-zones, in a road network the timing information of
users' entry and exit into the mix-zone and the non-uniformity in the
transitions taken at the road intersection provide valuable information to an
attacker trying to break the anonymity. We developed a suite of mix-zone
construction and deployment techniques that protect mobile users against location
privacy risks by offering both timing attack resilience and transition attack
resilience even when the mobility patterns and road-network topology are
exposed to the attackers.

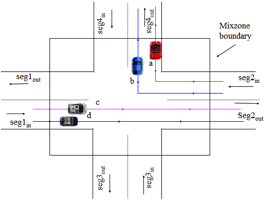
Figure 6:
Road Network Mix-zones for Anonymous Location-based Applications
Anonymizing Continuous Queries of Mobile users:
Continuous
location based services represent queries that are continuously evaluated along the trajectory of a mobile user either
periodically or aperiodically. While MobiMix road network mix-zone approach
works well against attacks based on road network characteristics, they are
vulnerable to attacks based on the temporal, spatial and semantic correlations
of location queries. To protect continuous query users, We developed three
types of delay-tolerant road network mix-zones (i.e., temporal, spatial and
spatio-temporal) that are free from CQ-timing and CQ-transition attacks and in
contrast to conventional mix-zones, perform a combination of both location
mixing and identity mixing of spatially and temporally perturbed user locations
to achieve stronger anonymity under the CQ-attack model. Based on experiments
on large scale geographic maps, we find that by combining temporal and spatial
delay-tolerant mix-zones, we can obtain the strongest anonymity for continuous
queries while making acceptable tradeoff between anonymous query processing
cost and temporal delay incurred in anonymous query processing. Overall, the
delay-tolerant mix-zone approach provides higher level of anonymity while
offering better quality of services for location based services with hard
continuity constraints.
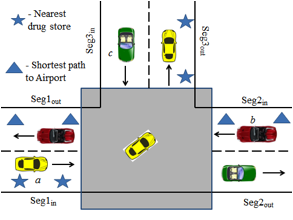
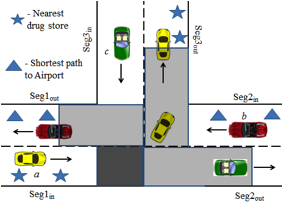
Figure
7:Continuous Query attacks on Rectangular and Non-rectangular Road Network
Mix-zones
Privacy-preserving Disclosure of Graph Datasets:
Most existing
privacy techniques protect the privacy of the individuals’ information while
providing the utility of the anonymized data in terms of aggregate results.
However, analytics on datasets providing accurate aggregate results may not
protect the privacy under scenarios where the aggregate information by itself
is sensitive, such as analytics related to business intelligence. Our framework
addresses this concern through the development of a new class of cryptographic
anonymization schemes which deals with anonymizing graph datasets to protect
utility at different levels such as graph structure, aggregate information and
invidual associations. Thus, the techniques offer the ability to provide privacy controlled data utility customized based on
per-customer access privilege levels. Thus, an important privacy enabling
technology for cloud
and outsourced data services is the ability to offer privacy
controlled data utility customized based on per-user access privilege levels
which cryptography driven anonymization schemes accomplish efficiently.
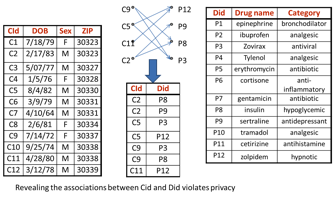
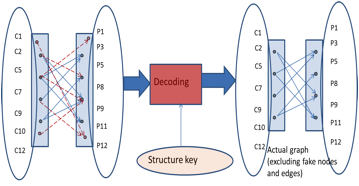
Figure 8:An
Example showing Cryptographic Anonymization and Decoding
Privacy-Preserving
Indexing for eHealth Information Networks:
The past few years have witnessed an increasing demand for
the next generation health information networks, which hold the promise of
supporting large-scale information sharing across a network formed by
autonomous healthcare providers. One fundamental capability of such information
network is to support efficient, privacy-preserving (for both users and
providers) search over the distributed, access controlled healthcare documents.
In this paper we focus on addressing the privacy concerns of content providers;
that is, the search should not reveal the specific association between contents
and providers (a.k.a. content privacy). We propose SS-PPI, a novel
privacy-preserving index abstraction, which, in conjunction of distributed
access control-enforced search protocols, provides theoretically guaranteed
protection of content privacy. Compared with existing proposals (e.g., flipping
privacy-preserving index), our solution highlights with a series of distinct
features: (a) it incorporates access control policies in the privacy-preserving
index, which improves both search efficiency and attack resilience; (b) it
employs a fast index construction protocol via a novel use of the
secrete-sharing scheme in a fully distributed manner (without trusted third
party), requiring only constant (typically two) round of communication; (c) it provides
information-theoretic security against colluding adversaries during index
construction as well as query answering. We conduct both formal analysis and
experimental evaluation of SS-PPI and show that it outperforms the
state-of-the-art solutions in terms of both privacy protection and execution
efficiency.
Related Publications:
· Balaji Palanisamy and Ling Liu, "Attack-resilient Mix-zones over Road Networks: Architecture and Algorithms" to appear in IEEE Transactions on Mobile Computing (IEEE TMC 2014). (Pdf)
· Balaji Palanisamy, Ling Liu, Kisung Lee, Shicong Meng, Yuzhe Tang, "Delay-tolerant Mix-zones on Road Networks", in Distributed and Parallel Databases (DAPD 2013). (Pdf)
· Balaji Palanisamy and Ling
Liu, "Effective Mix-zone Anonymization for Mobile Travelers”, in Geoinformatica 2013. (Pdf)
· Balaji Palanisamy and Ling Liu, "MobiMix: Protecting Location Privacy with Mix-zones over Road Networks", Proc. of 27th IEEE International Conference on Data Engineering (ICDE' 11). (Pdf)
· Balaji Palanisamy, Ling Liu, Kisung Lee, Aameek Singh and Yuzhe
Tang, "Location Privacy with Road Network Mix-zones", Proc. of 8th IEEE International Conference on
Mobile Ad-hoc and Sensor Networks (IEEE MSN'12). (Pdf)
· Yuzhe Tang, Ting Wang, Ling Liu, Shicong Meng, Balaji Palanisamy, "Privacy Preserving Indexing for eHealth Information Networks", Proc. of 20th ACM Conference on Information and Knowledge Management (CIKM' 11) (Pdf)
· Balaji Palanisamy, Sindhuja Ravichandran, Ling Liu, Binh Han and Kisung Lee, "Road Network Mix-zones for Anonymous Location Based Services", Demonstration at 28th IEEE International Conference on Data Engineering (ICDE' 13). (Pdf)
· Kisung Lee, Ling Liu, Shicong Meng, Balaji Palanisamy, "Road Network Aware Spatial Alarm Processing", Proc. of IEEE International Conference on Web Services (ICWS' 12). (Pdf)
· Kisung Lee, Ling Liu,
Binh Han, Balaji Palanisamy,
"ROADALARM: a Spatial Alarm System on Road Networks", Demonstration
at 28th IEEE International Conference on Data Engineering (ICDE'
13). (Pdf)
· Apurva Mohan , David Bauer, Douglas M. Blough, Mustaque Ahamad, Bhuvan Bamba, Ramkumar Krishnan, Ling Liu, Daisuke Mashima, Balaji Palanisamy, "A Patient-centric, Attribute-based, Source-verifiable Framework for Health Record Sharing", GIT CERCS Technical Report No. GIT-CERCS-09-11, 2009, Georgia Institute of Technology, Atlanta, GA, USA. (Pdf)
· Mustaque Ahamad, Douglas Blough, Ling Liu, David Bauer, Apurva Mohan, Daisuke Mashima, Bhuvan Bamba, Balaji Palanisamy, Ramkumar Krishnan, Italo Dacosta, and Ketan Kalgaonkar, "MedVault: Health Professional Access to Source-Verifiable Patient-Centric PHR Repository", at poster session in 19th Usenix Security Symposium, (USENIX Security' 10).
· Priyanka Prabhu, Shamkant B. Navathe, Stephen Tyler, Venu Dasigi, Neha Narkhede, Balaji Palanisamy, "LITSEEK: Public health literature search by metadata enhancement with External knowledge bases", in workshop of 18th ACM Conference on Information and Knowledge Management (CIKM' 09 ) (Pdf)